Security Basics for Non-Technical Builders Using Vibe Coding Platforms
 Sep, 2 2025
Sep, 2 2025
Why Your AI-Generated App Could Be Leaking Secrets
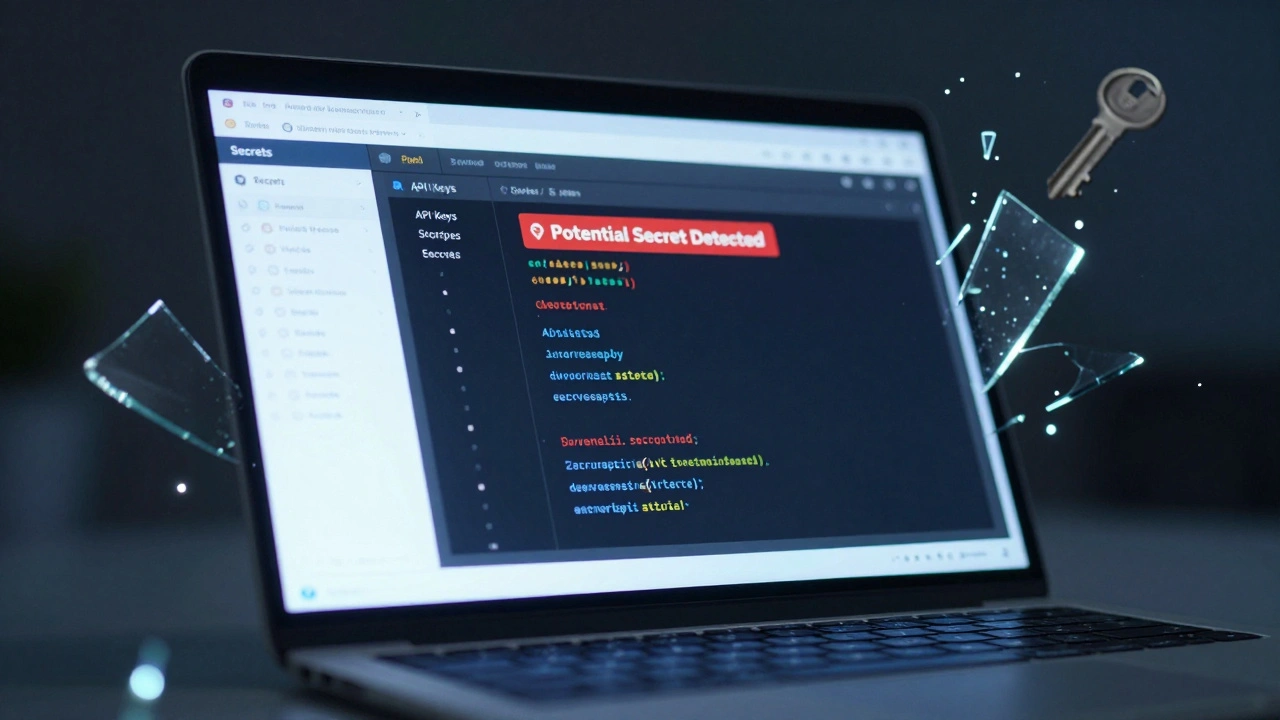
You built a website that works. It looks great. It runs smoothly. You didn’t write a single line of code yourself-just typed a prompt like, "Create a login page with Google sign-in and a contact form." And it did. That’s the power of vibe coding. But here’s the problem: that same app might be quietly leaking your API keys, database passwords, or customer data-and you have no idea. In 2025, over 24 million secrets were accidentally exposed on public code repositories, mostly from AI-generated code. That’s not a typo. That’s real. And most of it came from people like you: non-technical builders using tools like Replit, Bubble, or GitHub Copilot. You didn’t mean to break anything. You just wanted to get something live fast. But security isn’t optional anymore. If your app collects even one email address, it’s a target. The good news? You don’t need to be a developer to keep your app safe. You just need to understand a few non-negotiable rules.Never Hardcode Anything Sensitive
This is the #1 mistake. When you ask an AI to "add Stripe payments" or "connect to my database," it often replies with code that looks like this:const apiKey = "sk_live_abc123xyz";
That’s a live payment key. If that code ends up on GitHub-or even in your app’s source code-it’s public. Anyone can steal it. And they will.
In 2024, GitGuardian found that 78% of exposed secrets came from hardcoded values in AI-generated code. That’s not a glitch. That’s how these tools work by default. They don’t know what’s sensitive. They just give you the easiest answer.
Here’s how to fix it: use environment variables. Instead of writing the key into your code, you store it separately. In Replit, you click "Secrets" in the sidebar and add your key there. Then, in your code, you just write:
const apiKey = process.env.STRIPE_KEY;
The key stays hidden. The app still works. And you’re safe. Every vibe coding platform has a way to do this. Find it. Use it. Every time.
HTTPS Is Not Optional-It’s Automatic
If your site doesn’t start with https://, you’re not just vulnerable-you’re already compromised. Anyone can intercept your users’ passwords, credit cards, or messages if you’re using plain HTTP. Thankfully, most modern vibe coding platforms handle this for you. Replit, Vercel, and Webflow all serve your apps over HTTPS by default. You don’t have to configure certificates, buy SSL, or mess with settings. Just publish. Done. But here’s the trap: some platforms let you download your code or export it. If you move your app to a free hosting service like Netlify or GitHub Pages without checking, you might lose HTTPS. Always verify your live site URL starts with https://. If it doesn’t, fix it before you share the link.Sanitize All User Inputs
You added a contact form. Great. But what if someone types this into it:<script>stealAllData();</script>
If your app doesn’t clean that input, it could run that code on every visitor’s browser. That’s called XSS (cross-site scripting), and it’s one of the top three web vulnerabilities in 2025.
AI tools often generate forms without sanitization. You need to add it yourself. In Replit, you can use a simple library called DOMPurify. Just install it, then wrap any user input like this:
cleanInput = DOMPurify.sanitize(userInput);
You don’t need to understand how it works. Just copy the line. It’s like a filter that strips out dangerous code before it runs. Bubble.io and Webflow handle this automatically for their built-in form elements. But if you’re adding custom code-even a tiny bit-you must do this.
Version Control Is Your Safety Net
You’re probably using Git. Maybe without even realizing it. Replit and GitHub Copilot create repositories automatically. But here’s the problem: if you save your API keys in a file called .env and commit it to Git, you’ve just published your secrets to the world. The fix is simple: make sure .env is in your .gitignore file. That’s a tiny text file that tells Git: "Don’t track this." Most vibe coding platforms auto-generate this file for you. Check it. Make sure .env is listed. If it’s not, add it manually. GitGuardian says 32% of security incidents in vibe-coded apps happen because secrets were accidentally pushed to GitHub. That’s preventable. In 89% of cases, just having a proper .gitignore file stops it before it starts.Know What Counts as a Secret
Not all secrets are obvious. Here’s a quick list of what to watch for:- API keys (Stripe, Google Maps, Twitter, etc.)
- Database passwords
- JWT tokens or session secrets
- Cloud storage credentials (AWS, Firebase)
- OAuth client IDs and secrets
Choose the Right Platform
Not all vibe coding tools are built the same. Here’s what you need to know:| Platform | Auto HTTPS | Secret Management | Input Sanitization | Auto .gitignore | Security Scanning |
|---|---|---|---|---|---|
| Replit | Yes | Yes (built-in Secrets) | Yes (via library) | Yes | Yes (blocks 92% of common flaws) |
| Bubble.io | Yes | No (manual setup) | Yes (for built-in elements) | Yes | No |
| GitHub Copilot | No (you provide hosting) | No | No | Yes (but only if you set it up) | No |
| Webflow | Yes | No | Yes | Yes | No |

What Happens When You Ignore This
Real stories. Real damage. One user on Reddit, "MarketingMike," built a simple landing page with AI. He hardcoded his Google Ads API key. Within 48 hours, someone used it to run $3,200 in fake ad campaigns. His account was locked. He lost money. He lost trust. Another person used Bubble.io to build a SaaS tool. They hardcoded their Stripe key. Hackers drained $1,850 in fraudulent transactions before they noticed. These aren’t rare. They’re routine. The Verizon 2025 Data Breach Report says 43% of breaches from no-code tools come from misconfigured authentication. Another 37% come from exposed secrets. You’re not a target because you’re big. You’re a target because you’re easy.Start Safe, Not Sorry
You don’t need to learn to code to be secure. You just need to follow five rules:- Never type secrets into your code. Use environment variables.
- Always check your site URL starts with https://.
- Sanitize user inputs with DOMPurify or your platform’s built-in tool.
- Confirm .env is in your .gitignore file.
- Use Replit or another platform that handles security automatically.
Frequently Asked Questions
Do I need to pay for security features in vibe coding platforms?
No. Core security features like HTTPS, secret management, and .gitignore are free on platforms like Replit. You only pay for extra storage, traffic, or advanced features like custom domains. Security basics are included in the free tier for everyone.
Can I use GitHub Copilot safely?
You can, but you’re on your own for security. GitHub Copilot generates code but doesn’t scan for secrets, enforce HTTPS, or auto-protect inputs. You must manually add environment variables, sanitize inputs, and check your .gitignore. It’s powerful, but it’s also riskier than platforms designed for non-technical users.
What if I already published my app with hardcoded secrets?
Act fast. First, rotate all exposed keys-go to your API provider (Stripe, Google, etc.) and generate new ones. Then, remove the old keys from your code. Push a new version. Finally, check your .git history to make sure the secrets aren’t still in past commits. Use tools like GitGuardian’s free scanner to double-check.
Is vibe coding allowed in my company?
Many companies now allow it-68% of Fortune 500s do, according to Forrester. But they require security training. If you’re building for work, check your company’s policy. Even if it’s not written down, following these five rules will make your project acceptable.
Will AI start fixing these security issues automatically?
Yes, and it’s already happening. Replit’s AI now blocks 92% of common vulnerabilities before you deploy. GitHub added real-time secret detection in February 2025. By 2026, regulated industries will require AI-generated code to pass security checks before deployment. The tools are catching up-but right now, you still need to know the basics.
E Jones
December 8, 2025 AT 17:58Okay so imagine this: your AI-generated app is basically a neon sign screaming "HACK ME" with your API keys painted in glitter and blood. I once saw a dude use Replit to build a "simple" landing page and his .env file ended up on GitHub with his Stripe key, his Firebase creds, and his ex’s birthday. Yeah. That’s not a mistake. That’s a public service announcement for cybercriminals. And now he’s got a $12k bill from Stripe because someone used his key to buy 47 virtual gold-plated NFTs of a crying cat. And the worst part? He thought "environment variables" were a type of yoga pose. We’re not just building apps anymore-we’re building landmines for our own future selves. And nobody’s teaching this stuff. Not in school. Not in YouTube tutorials. Just here, in the trenches, where the real hackers are just waiting for the next clueless vibe coder to hit publish.
Barbara & Greg
December 10, 2025 AT 13:57It is both tragic and profoundly irresponsible that individuals, lacking even the most rudimentary understanding of digital security, are being encouraged to deploy applications that handle sensitive user data. The normalization of "vibe coding" as a legitimate development practice represents a dangerous erosion of professional standards. The notion that one can bypass foundational knowledge-such as the distinction between client-side and server-side execution, or the imperative of input sanitization-and still claim to be a "builder" is not innovation; it is negligence. The responsibility for protecting user data does not vanish because one uses a drag-and-drop interface. It intensifies. And yet, the prevailing culture glorifies speed over safety, convenience over consequence. This is not progress. It is precarity dressed in a hoodie.
selma souza
December 12, 2025 AT 02:12"Never hardcode anything sensitive"-this sentence contains a grammatical error. It should be "Never hardcode *any* sensitive information." "Anything" is not a countable noun in this context, and "secrets" are information, not objects. Also, you wrote "HTTPS Is Not Optional-It’s Automatic"-the hyphen is incorrectly used. It should be an em dash or a comma. And you say "use DOMPurify" but never link to the official documentation or specify version compatibility. This article is dangerously misleading because it prioritizes tone over precision. If you're teaching security, you must be exact. Otherwise, you’re not helping-you’re enabling.
James Boggs
December 13, 2025 AT 06:06Great breakdown. I’ve seen too many people blow past these steps because they just want to ship something. The Replit Secrets feature is a game-changer-so simple, so effective. If you’re just starting out, use it. Don’t overthink it. Just add your keys there, and you’re 90% safer already. Also, double-check your live URL. Always. One time I missed https and shared a link for weeks before realizing. Oops. But now I check every time. Small habits save big headaches.
Addison Smart
December 13, 2025 AT 10:07I come from a background where security was drilled into us like a religion-firewalls, encryption, zero trust, audits, compliance. But I’ve also watched non-technical creators build beautiful, functional tools that changed lives without ever touching a terminal. The beauty of this post is that it bridges that gap. It doesn’t demand you become a developer. It just asks you to respect the invisible wires beneath the interface. The platforms that handle secrets, HTTPS, and sanitization automatically aren’t just convenient-they’re ethical. They’re saying, "We know you’re not a pro, but your users deserve protection anyway." That’s not just good design. That’s human-centered tech. And if we’re going to democratize building, we have to democratize safety too. Replit leads because it doesn’t assume you know better. It assumes you care-and then makes it easy to act on that care. That’s the future.
David Smith
December 14, 2025 AT 21:23Ugh. Another "do this, don’t do that" lecture from someone who clearly has never tried to build anything real with AI. I made a todo app in Bubble with Google login and it works fine. No one’s hacked me. Maybe the real problem isn’t vibe coding-it’s people who get off on scaring everyone into panic mode. You say "24 million secrets exposed"-but how many of those were from people who actually had customers? Or were they just dev test keys uploaded by bored college kids? I’m not saying security doesn’t matter. But this post reads like fear porn wrapped in a tutorial. If you’re building something for fun, don’t stress. If you’re building for real people, then yes, learn the basics. But don’t make the rest of us feel like criminals for using tools that work.
Michael Jones
December 15, 2025 AT 13:45Security isn’t a checklist it’s a mindset you don’t need to be a hacker to protect people you just need to care enough to check the URL to make sure it says https and to not copy paste magic strings into your code like they’re confetti at a parade the tools are getting smarter but the people still have to be awake you’re not building a website you’re building a trust and if you break that you break something way bigger than code